HOME / S2P Software Implementation / Sustain
Sustain
Cloud Infrastructure Operations, Security & Governance
Ensuring Complete Protection and Seamless Operation of Your Data
The Sustain phase of our SCALE methodology focuses on robust cloud infrastructure operations, security, and governance. Zycus ensures complete protection of your data, leveraging advanced encryption methods and stringent access control mechanisms to maintain the highest levels of security and operational efficiency.

Zycus’ Value Delivery Framework
SCALE framework to ensure implementation success
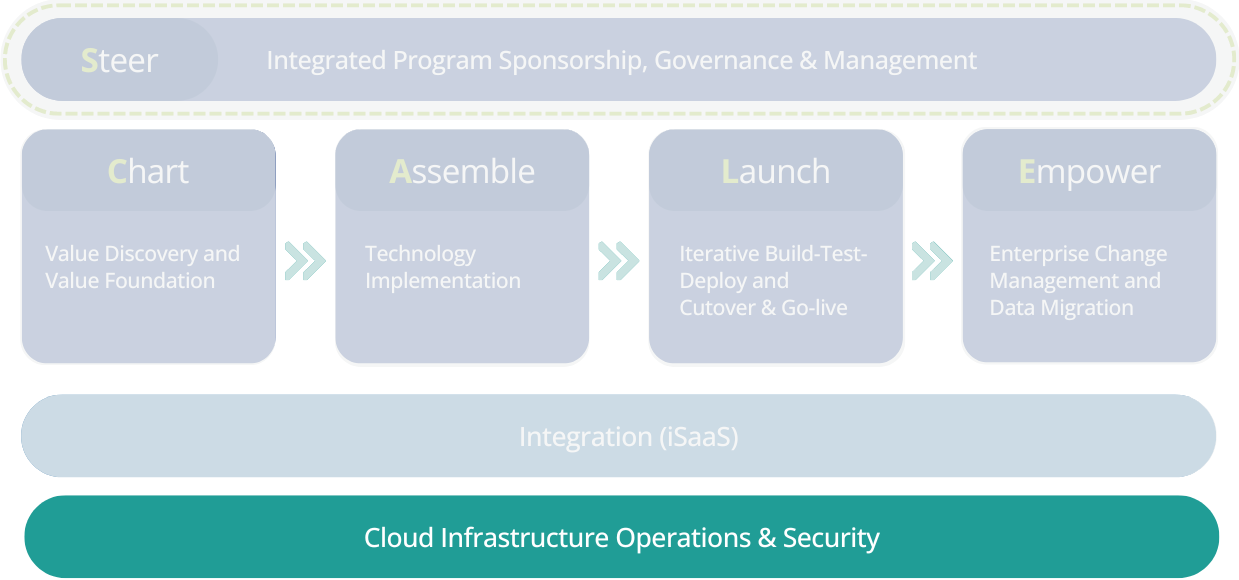
Key Features of Sustain

Cloud Infrastructure Operations
- Elastic Scaling: Automatically scale resources up or down based on demand.
- High Availability: Ensuring continuous availability with minimal downtime.
- Performance Optimization: Optimizing cloud resources for peak performance.
Security & Governance
- File-Based Encryption: Using PGP & AES encryptions to protect file-based data.
- API-Based Encryption: Employing 2048-bit SSL and token-based access for API-based data.
Access Tokens Authentication (Two-Factor)
- Temporary Access Tokens: Valid for 8 hours from the time of issue.
- Encrypted Challenge: Request an encrypted challenge that can be decrypted with a shared secret PIN.
- Secure API Calls: Make API calls with the decrypted challenge as the signature's secret key.
- AUTH String: Computed as a Base 64 encoded string of "username
- API Calls: Make API calls with the AUTH string as the signature's secret key.
- Recommendation: Zycus recommends Two-Factor authentication over Basic Authentication for enhanced security.
- Client Registration: Register the client application and obtain a unique application ID.
- Challenge Request: Make a Challenge Request and decrypt the challenge.
- Access Token Request: Request an Access Token using the decrypted challenge and receive the token.
- API Calls: Make GET/POST calls using the Access Token, valid for 8 hours.
- Concurrency Control: Restricting the number of concurrent calls to 10 per application ID, requiring a queuing mechanism for optimal performance.
- Token Expiry: Existing tokens expire as soon as a new token is issued or after 8 hours.

Detailed Security Measures

Encryption Methods
- Data Protection: PGP (Pretty Good Privacy) and AES (Advanced Encryption Standard) provide robust encryption for file-based data, ensuring it is protected from unauthorized access.
- Secure Communication: Using 2048-bit SSL for secure API communication.
- Token-Based Authentication: Implementing token-based access to control API usage and enhance security.
Access Tokens Authentication Process
- Request Encrypted Challenge: Obtain an encrypted challenge that can be decrypted with a shared secret PIN.
- Request Access Token: Use the decrypted challenge as the signature's secret key to request an Access Token.
- API Call Execution: Make API calls with the decrypted challenge as the signature's secret key, with tokens valid for 8 hours.


Best Practices for API-Based Integration
- Register Client Application: Obtain a unique application ID for secure API integration.
- Decrypt Challenge: Make and decrypt the Challenge Request.
- Access Token Utilization: Use the Access Token for making secure API calls within the 8-hour validity period.
- Concurrency Control: Restrict concurrent calls to 10 per application ID to ensure optimal performance.

Source to Pay integrations easier than ever!
Learn more about our cloud infrastructure operations, security, and governance strategies
01
Comprehensive Integrations:
Seamless data flow to connect
ERP, procurement, and financial
systems
02
Data Security and
Compliance: Data protection
using advanced security
protocols
03
Scalable and Flexible
Architecture: Future proofs
integration strategy using
adaptive scalable architecture
As organizations navigate through the complexities of modern procurement, the zycus procure-to-source system emerges as a transformative force. It integrates seamlessly, offering end-toend visibility, enhanced supplier relationships, and data-driven insights. with Zycus, businesses unlock the power to drive efficiency, mitigate risks, and achieve strategic objectives, paving the path for sustainable success in today’s dynamic marketplace.
Chris Loveland
Global Procurement Operations Leader
Belden

Tech support from all the corners
Zycus implementation ensures delivery excellence at SCALE supported by relevant tools and technologies that make the whole infrastructure risk free.

What sets Zycus’ Customer Value Delivery Solutions Apart?
01
Agile Deployment: Rapid,
flexible responses to change.
02
Critical Success Factors (CSF)
Focus: Ensuring alignment with key business priorities.
03
Advanced Tech Stack:
Streamlining processes with
cutting-edge tools.